Schema Private Registry
Private Schema Registry is only applicable for Federated Schema, not Single Schema configurations.
In the rare event of a service, network, or Internet outage, newly published federated schemas may not be accessible through the Inigo cloud from your GraphQL gateway (Apollo Gateway/Router). By deploying your private schema registry, you can maintain your federated schemas within your network so there is no interruption in service for pulling those federated schemas.
Architecture
Figure 1 shows the architecture for how Inigo handles federated schema deployments with a Private Schema Registry. The Private Schema Registry will connect back to the Inigo Control Plane to pull down the latest Composed Schemas as they are published.
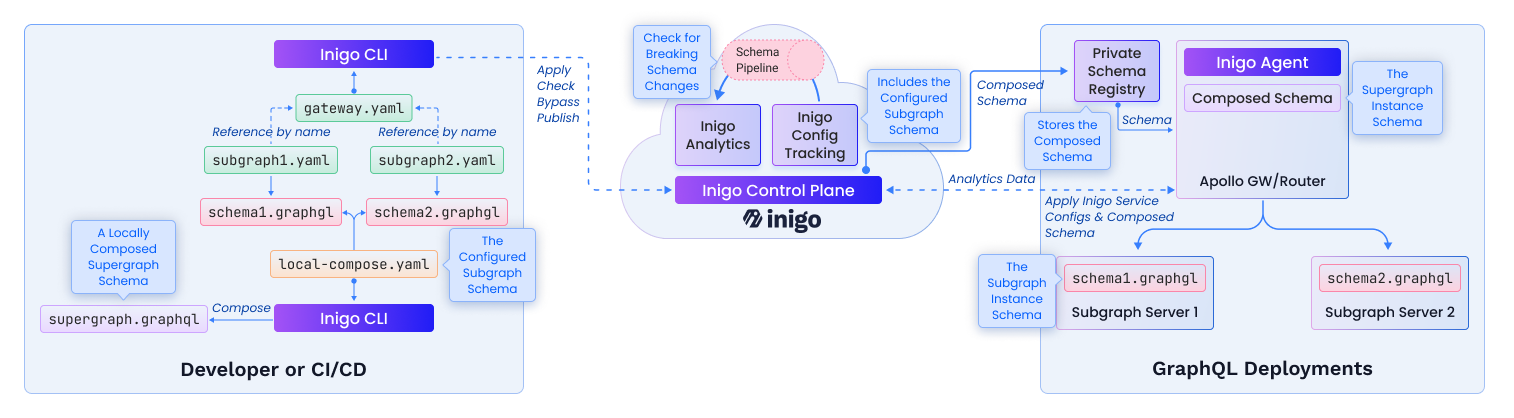
Figure 1. Inigo Schema Management Architecture (Private Configuration)
Create a Private Schema Registry
A Private Schema Registry can be created using the Inigo CLI using inigo create registry. After creating the Private Schema Registry, a token value must be retrieved with inigo create registry token, as shown in Example 1.
inigo create registry --url=http://localhost:9000 my-registry
inigo create registry token my-registry
Example 1. Create a Private Schema Registry.
Expected output from Example 1:
registry token created: eyJhbGciOiJIUzUxMiI...
Run the Private Schema Registry
The Private Schema Registry can run as a Docker container and can be configured to use various storage methods such as S3, GCS, or simply a mounted volume.
Example 2 demonstrates how to run using INIGO_STORAGE_PATH, which simply stores the schemas in a mounted volume.
export INIGO_REGISTRY_TOKEN=ey...
docker run -d \
-e INIGO_REGISTRY_TOKEN=$INIGO_REGISTRY_TOKEN \
-e INIGO_STORAGE_PATH="/var/inigo_registry" \
-e INIGO_LISTEN_PORT=9000 \
-e LOG_LEVEL=debug \
-v /tmp/inigo_registry:/var/inigo_registry \
-p 9000:9000 inigohub/inigo_registry
Example 2. Run the Private Schema Registry using INIGO_STORAGE_PATH set to /var/inigo_registry.
Private Schema Registry Run Configurations
There are three ways to configure the storage of the registry (local volume, GCP GCS, AWS S3), and only one should be used.
| Config Value | Type | Description |
|---|---|---|
INIGO_REGISTRY_TOKEN | string (required) | The token value retrieved from inigo create registry token |
INIGO_LISTEN_PORT | string (default: 80) | The port that the Private Schema Registry listens |
INIGO_STORAGE_PATH | string | The path to the volume where the registry will store schemas and is only needed for the local volume option |
Private Schema Registry AWS S3 Configurations
If you are running the Private Schema Registry in AWS, you can leverage AWS S3 Buckets to store the schemas.
The buckets must have read/write permissions for the container running the Private Schema Registry. This can be accomplished using IAM rules.
| Config Value | Type | Description |
|---|---|---|
INIGO_STORAGE_AWS_ENABLE | string (default: false) | true or false to enable the AWS storage configuration |
INIGO_STORAGE_AWS_BUCKET_NAME | string | Name of the S3 bucket that will store the schemas |
INIGO_STORAGE_AWS_REGION | string | The AWS region for the bucket |
Private Schema Registry GCP GCS Configurations
If you run the Private Schema Registry in Google Cloud Platform (GCP), you can leverage Google Cloud Storage (GCS) Buckets to store the schemas.
The buckets must have read/write permissions for the container running the Private Schema Registry. This can be accomplished using IAM rules.
| Config Value | Type | Description |
|---|---|---|
INIGO_STORAGE_GCS_ENABLE | string (default: false) | true or false to enable the GCS storage configuration |
INIGO_STORAGE_GCS_BUCKET_NAME | string | Name of the GCS bucket that will store the schemas |
INIGO_STORAGE_GCS_PROJECT_ID | string | The Project ID that contains the GCP bucket |
INIGO_STORAGE_GCS_STORAGE_CLASS | string | The storage class for the bucket |
INIGO_STORAGE_GCS_REGION | string | The GCP region for the bucket |
Configure the Private Schema Registry in the Gateway's Service
As documented in Federated Schema, a Gateway is set up to configure your gateway deployment and the associated subgraphs. In tandem with the Gateway,
a Service of the same name and label must also be created to associate the Private Schema Registry to the gateway deployment.
As shown in Example 3, a Service that has the same name as the Gateway must be defined with a registry name configuration.
kind: Service
name: apollo-gateway-fed-2-demo
label: dev
spec:
registry: my-registry
Example 3. Set up the Service association for the Private Schema Registry.
The Service configuration can be applied as such:
inigo apply service-gateway.yaml
The expected output of running inigo get registry will now show the associated SERVICES output, as shown in Example 4.
inigo get registry
NAME URL SERVICES
---- --- --------
my-registry http://localhost:9000 apollo-gateway-fed-2-demo:dev
Example 4. Run inigo get registry to see the associations of the services to the Private Schema Registry.
Configure Apollo Gateway to use the Private Schema Registry
If you use Apollo Gateway, the InigoSchemaManager's endpoint parameter must be configured with a INIGO_REGISTRY_URL, as shown in Example 5.
import { Inigo, InigoRemoteDataSource, InigoSchemaManager } from "inigo.js"
...
const gateway = new ApolloGateway({
supergraphSdl: new InigoSchemaManager({
endpoint: INIGO_REGISTRY_URL,
}),
...
});
Example 5. Configure Apollo Gateway to use INIGO_REGISTRY_URL.
With this configuration, the Inigo Agent running inside of the Apollo Gateway deployment will connect to the Private Schema Registry to pull down the schemas as new versions are published.
A demo application demonstrates how Apollo Gateway can be configured for the Private Schema Registry.
Configure Apollo Router to use the Private Schema Registry
If you are using Apollo Router, the configuration for the Private Schema Registry is straightforward, just the INIGO_REGISTRY_URL needs to be set when running Apollo Router. See the Apollo Router documentation for further details.